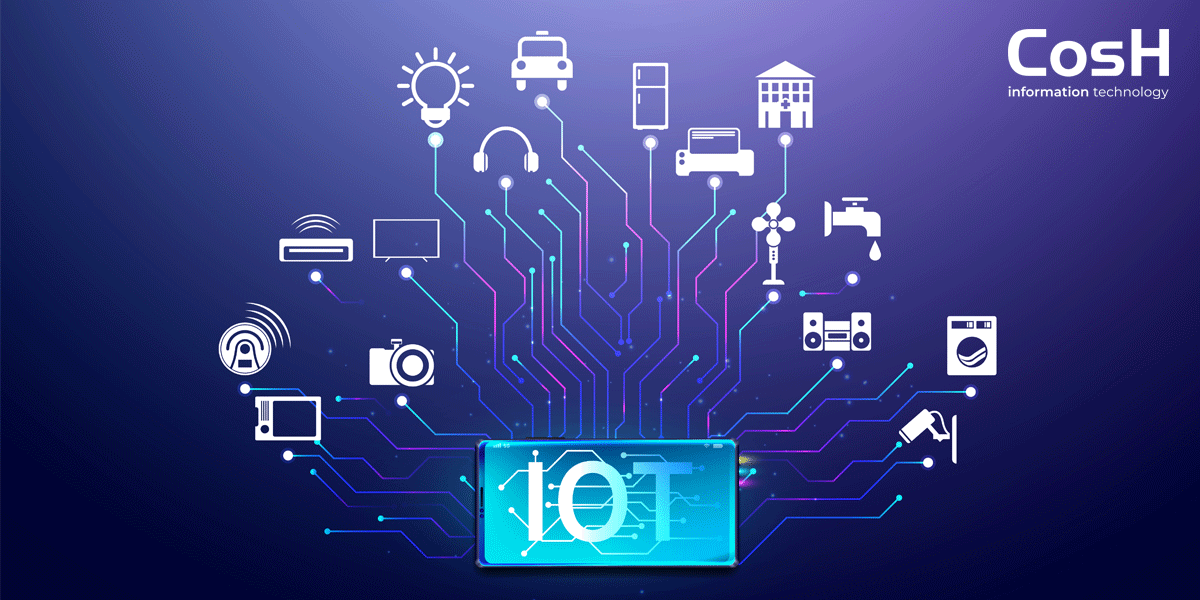
“The Internet of Things” (IoT) is unstoppable. More and more devices are becoming packed with technology and smart. However, there are many security gaps, especially in the area of building technology. Due to poorly secured and structured networks, attacks on infrastructures are on the rise. Statista predicts more than 75 billion connected devices by 2025. A study by Paloalto Networks shows it: 98 percent of IoT data traffic is handled unencrypted, making it interesting for cyber attacks. Printers and surveillance cameras also count as IoT devices. The security vulnerabilities in such devices are the ideal gateway for cybercriminals. The devices themselves are usually of no interest to them – they serve as door openers to access other IT systems in the company. Basically, anything connected to the Internet is at risk. In particular, control and regulation systems of building technology systems are among the most popular targets of attack. In any case, one thing is (in)certain: the more the Internet of Things and its IoT devices gain importance in companies, the higher the risk that these devices will be misused for criminal actions. Unfortunately, search engines like shodan.io can be used to locate network devices and open ports worldwide.
Network segments as secure separation between IoT and corporate network
First, what is network segmentation anyway? Here, the corporate network is divided into individual areas to ensure greater IT security and better administration options. Consequently, IoT devices should definitely be outsourced to their own network. IT security experts recommend strict separation between the “normal” corporate network and that of the IoT devices. This way, employees’ computers are isolated in a separate network and cannot be attacked via cameras, printers, doorbell systems, etc. Likewise, of course, the other way around: employee computers cannot be used as a springboard to attack IoT devices. The connection between the network segments is kept as low as possible. You probably know this from WLAN networks. Companies often have guest networks that are completely isolated from the internal network and are specially secured. As a rule, networks should be segmented according to the company’s criteria and security requirements. Particularly in industrial operations and Industry 4.0, entire production lines need to be safeguarded.
However, network segmentation is not only useful when deploying IoT devices: clients should be separated from servers and, at the same time, externally accessible services such as e-mail or web servers should be operated in a so-called demilitarized zone (DMZ). This has the decisive advantage that if, for example, passwords fall into the hands of cybercriminals, the damage is limited only to individual network segments and not to the entire corporate network.
Network segmentation is not a one-time task. Rather, it is an ongoing process to maintain steady IT security. We would like to point out here that these represent only one part of a holistic IT security concept.
Conclusion: With the Internet of Things, more and more intelligent and networked devices are entering everyday business life. But the security risks should not be ignored.